- Free Decrypt Software
- Conax Decrypt Software Download
- Conax Decrypt Software
- Conax Decrypt Software Free
Decrypt Encrypted NSF Files at Local |
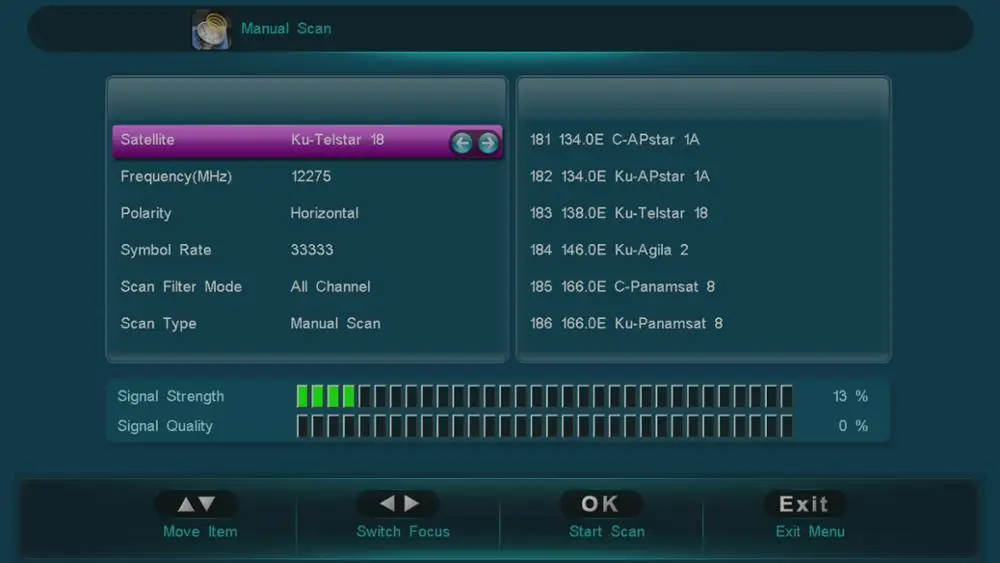
Conax Key Software. (CAM) is a combination of encryption keys, smartcards and electronics and computer code inside a satellite or cable-TV receiver (or “decoder”). The pay-TV provider encrypts the digital signal sent to the subscriber with an encryption key. The subscriber plugs a smartcard into his/her decoder, which. Conax Decrypt Software Broadcom Bcm43xx Driver Mac Os X Arahweave software, free download Free Manfred Spitzer Digitale Demenz Rapidshare Movies. March 29, 2012 1. During the smart card personalization stage decryption of consumer database records fixed.Encryption of working loads of the conditional aproach messages (ECMs and EMMs) engender at the end.The Irdeto Key Server based on forwards technologies, dellivers operators with the highest point of security, whilst simplifying operational management.For.
- Most multiple format CAMs and all CAMs that directly decrypt a signal are based on reverse engineering of the CA systems. A large proportion of the systems currently in use for DVB encryption have been opened to full decryption at some point, including Nagravision, Conax, Viaccess, Mediaguard (v1) as well as the first version of VideoGuard.
- Conax and related information Frankensaurus.com helping you find ideas, people, places and things to other similar topics. Topics similar to or like Conax. Conax develops television encryption, conditional access and content security for digital television.
Securase comes with group mode ability easily decrypt encrypted NSF Files at local. How open NSF Files? This query can be effortlessly solved with NSF opener that simply removes NSF security without damaging, free NSF data from all restrictions. Software give rights to do operations such as open, read, view and modify without destruction of any data from Notes Storage Format.Users easily deal effectively with NSF error messages such as: ‘Lotus Notes has local access protection and you are not authorized to access that database’ or ‘you are not authorized to perform that operation’ with Securase software. But point should be noted that this NSF file local encryption remover tool remove only local security from Notes NSF files and not supported to remove password from NSF files.Download illustrating the feature process of local security remover software for Notes tool freeware, it remove security from some NSF files providing by Lotus Notes database. If you would like to remove NSF encryptions from unlimited protected NSF file, get the full pro version of the tool only at $49. Read more info: http://www.removensfsecurity.org/decrypt-encrypted-nsf-files-local.html |
| Системные утилиты – Управление файлами и дисками | |
| 3.5 | |
| 24.12.13 | |
| Windows | |
| Shareware (49 USD, 36 EUR) | |
| Decrypt Encrypted NSF Files at Local | |
| 25.10.14 | |
| 25.10.14 | |
| Win2000 Win7 x32 Win98 WinOther WinServer WinVista WinVista x64 WinXP | |
| 740 КбСкачать программу Decrypt Encrypted NSF Files at Local 3.5 | |
| не присвоен | |
| 412 | |
| 107 |
Decrypt Encrypted NSF Files at Local 3.5 |
Decrypt Encrypted NSF Files at Local 3.5?
Популярные запросы
Скачать Cydia
Registry Clean Master улучшает производительность.

Получите официальные драйверы Bluetooth для Windows 7
Cydia - бесплатный магазин приложений
Утилита, открывающая файлы с расширением MDF
Download user albums from Instagram.
Turn your HP notebook into wireless router.
Free Photo Booth Effects Software.
Matrix calculator.
Create flash page flip books from MS Word
Convert multiple ODTs to Docs.
Амазонские шахматы
Mobogenie is a Free Android Phone Manager
WebAPP Web Automated Perl Portal, cms.
Open, View and Print any Excel(Xls,Xlsx) files
Convert PDF to doc, PDF to DOC files.
Optimize, Clean, Speed Up
Создавайте флип-буки и флэш-страницы из MS Ofice
Turn your laptop into a wireless access point
Windows 7 Cleaner - пакет программ для оптимизации компьютера
Утилита для автоматического клика мышкой
Press Release Script - Own Press Release Site
Turn your iPhone into a wireless mouse!
Программа для парсинга 2ГИС
share to your friends,groups and pages
An easy and efficient FREE mp3 cutter.
PicJet Studio - мгновенная обработка фоток
play MP4 and FLV videos simply.
SQL Recovery Tool for SQL Error Fix Process
Решить это весело головоломки и выигрывайте!
Video Wallpaper
Утилита, открывающая файлы с расширением MDF
Fat32Format поддержка до 2 Тб объем байт
Быстро открыть любой файл DMG на Windows PC
Office 365 Office 365 миграции решение
Легко получить доступ к любимым папкам
ExFAT Разделов, Инструмент Для Восстановления Удаленных Данных
CheckDisk-это мощный инструмент для поиска
Convert MS Word 2007 to 2003 via Docx Repair
Скачать бесплатно лучшие VCF to XLS Converter Tool
Convert JPG JPEG image into Adobe Acrobat PDF
PowerPoint 2003 to 2010 Converter и 2007
На халяву: увеличить срок службы ваших SSD!
Email восстановление из Outlook Express
Adobe редактор для редактирования данных из Adobe PDF
XML, HTML, HTM, TXT, PHP to PDF converter.
Просто читать контакты из Outlook в vCard
Программа ремонта
Запись NTFS-файлов в среде Mac OS

Microsoft Outlook 2003 Ремонтной Программы Утилиты
Лучший способ восстановить поврежденные видео файлы
Microsoft Word Document Recovery software.
Находчивый документ Adobe PDF редактор
Auto Detect
Новый Диск управление продуктами
Open Outlook Express Files to Repair DBX File
Best DBX to PST Conversion Software
Get Effective Excel to vCard Converter
ScanPST Exe Outlook 2003 Software
Экспорт NSF Adobe PDF инструмент преобразования
Free Decrypt Software
Лучшее программное обеспечение для восстановления Microsoft Word файл
Powervu – latest tech to watch premium channels on big dish on strong decoders. Got a CAS3 programmer and a T-rex 4.6, a Magic Module and a X-cam. I need to 'program' one of these cams so I can use my original Conax card. I was told that the T-Rex CAM could do it but cannot find any software to load. Il primo decoder certificato per l'alta definizione in digitale terrestre TELE System presenta il decoder interattivo TS7900HD, un ricevitore di altissimo contenuto.
Over the last couple of days a small furore has erupted a News Corp subsidiary, has been hacking the pay-TV smartcards of News Corp’s competitors, and even News Corp’s own companies – allegations that NDS. I’m not going to speculate on the reasons why a supplier of – the technology that allows paid-TV providers to restrict access to their broadcasts – would want to undermine the security of their own product; but I am going to discuss how such systems work, and how secure they are. A Conditional Access Module (CAM) is a combination of encryption keys, smartcards and electronics and computer code inside a satellite or cable-TV receiver (or “decoder”). The pay-TV provider encrypts the digital signal sent to the subscriber with an encryption key. The subscriber plugs a smartcard into his/her decoder, which decrypts the signal so programs and films can be displayed on the screen.
Some decoders have the smartcard built-in already, so there is no external slot. The is a plastic card with a chip - much like a modern credit card.
You can see electrical contacts on the chip. When the card is inserted, the chip is plugged into the decoder, allowing the CAM to get the decryption key. Other information is also stored on the chip – subscriber ID, subscription details, billing details, censorship filters and so on. We don’t really know what’s there unless we hack into the chip, because it’s all kept secret. Each chip will have it’s own non-volatile memory (requires no battery), computer programs and a small (CPU).
Conax Decrypt Software Download
The security of the system depends on a few things:. secrecy of the encryption algorithm. secrecy of the keys.
secrecy of the hardware. So let’s start with the.
An algorithm is a recipe for doing something – in this case, for scrambling and descrambling the digital signal. Some CAM providers write their own algorithm, and depend on it remaining a secret. That’s a bit like hiding your door key inside a brick or under a flower pot – once the secret (that the key is in the brick) is discovered, you have no security. Works this way. A much better approach is to keep the key with you (a secret key). Everybody knows how your door security works (you put the right key in the lock and turn), but that only works if you have the key. If your lock (algorithm) is faulty, you’ll find out quickly enough and replace the lock.
Of course, Pay-TV subscribers would have to remember the key, and have to enter it into their decoder - very inconvenient, but very safe. Foxtel uses CAMs. These use encryption - a reasonably complex encryption algorithm that’s difficult to crack without employing lots of supercomputers. 3DES is a known algorithm - it has been tested for years and, if implemented correctly, will be safe.
And the security of the decryption key? That’s stored on the chip in the smartcard. Just like hiding it inside a (very thin) brick. 3DES is a, which means you use the same key to encrypt and decrypt. If hackers can open up the card and get to the key, they can extract the key and use it to make cloned cards. This leads us to the secrecy of the hardware. Four years ago, Wired magazine posted a YouTube video (see below) showing Chris Tarnovsky demonstrating how to extract the chip from a smartcard, and access the electrical signals.

Reprogramming the card to display its stored data (including the decryption key) is the next step. Modern cards are better, but the techniques for getting into them are also better. It’s not even necessary to open up the card. Many digital TV watchers use techniques such as card sharing or to spread the cost of a Pay-TV subscription among tens or hundreds of people. And you can buy blank smartcards online from places such as for a few cents each.
Conax Decrypt Software
There are also dedicated forums online to help would-be criminals access satellite TV and Pay-TV without a subscription. Just Google terms such as, and (Modified Original Smart Card). So just as with (circumventing the built-in security mechanisms of the Xbox and Xbox 360 videogame consoles), (gaining “superuser” permissions to your Android device’s software) and iPhones (gaining root access to Apple’s operating system), pay-TV piracy/hacking is happening now. The information is out there and is easy to access. Of course, anyone attempting to use the information has to be technically capable and adventurous.
Is it being done on an industrial scale? Perhaps in places such as China or South America. A lot of the hardware which enables or supports unlawful access to IT systems (e.g. – the illegal copying of information from the magnetic strip of a credit or ATM card) appears to be coming from those regions.
Conax Decoder Software Pc
Conax Decrypt Software Free
The Chinese government is and the systems which support it. My opinion is that the skills required (to hack these smartcards) are beyond most wannabe pirates and hackers. Besides, it’s much easier just to install the peer-to-peer file-sharing protocol and download any program or film you want.